justinbentley.dev
- jbn.ai
- jbn.ai/aa (Aphid Attack)
- pcuser.org
- arcaneww.com (Arcane Woodwork)
- wodenldc.com.au (Woden Laundromat)
- justinbentley.net
- react.justinbentley.net
- dennisbentley.net
- justinbentley.dev
- davidgreenmusician.com
- renderedlandscapes.com
- AWS / EC2 Windows Server
- IIS Configuration
- GateKeeper
- File Server
- IISOnline
- FRTLibrarian
- NeRV (.Net Runtime Versions)
- AbuseIPDB API (Tester)
- ImageViewer.js
- glparticlegen.js
- Cookies.js
- fs.js
- SQL / T-SQL / MSSQL Database
- DatabaseSecurity
- VR Tai Chi
- bubbles!
- VIC Final Assignment
- .obj Wavefront Mesh Importer
- Legacy (v1.2) OpenGL Guide
- Training Room (Autodesk Maya)
- USS-199
- Save the Trees
- CodeLiner
- Subtitle (.srt) Time Stamp Reducer
- Payroll System
- Sleep
- Gross Calculator
- ANN (AI) 1
- ASCII Dictionary
- Timer
- xUnitTest
- StarBase BASIC
- Digital Circuitry
- Very Long URL Expertise
Website Development
 Switchboard: jbn.ai
Switchboard: jbn.ai
.Net Core 8, MVC
HTML, CSS, JavaScript, SPA, WebGL (three.js), GLSL (C), glTF (.glb), Media Queries, Cookies
3D Frontend, Switchboard site.
Large client-side JavaScript engine to operate multiple WebGL backgrounds and dynamically switch icons.
Includes my own polymorphic JavaScript three.js Particle System with its own GLSL (C-like syntax) Particle Shader.
Unminified.
 Aphid Attack (game): jbn.ai/aa
Aphid Attack (game): jbn.ai/aa
.Net Core 8, Blender
HTML, CSS, JavaScript, WebGL (three.js), glTF (.glb)
3D WebGL Game.
WebGL Game Engine, Game, Keyboard / Mouse Control, everything in vanilla JavaScript and three.js.
Hope you like it!
 pcuser.org: pcuser.org
pcuser.org: pcuser.org
.Net Core 8, MVC, Blender
HTML, CSS, JavaScript, WebGL (three.js), glTF (.glb), Cookies, Figma
PC (Personal Computer) issue site.
Uses Cookies to store client last state on index page and theme preference.
 Arcane Woodwork: arcaneww.com
Arcane Woodwork: arcaneww.com
.Net Core 8, MVC, API Dynamic Image Viewer, ReCaptcha
HTML, CSS, JavaScript, Media Queries
Woodwork Showcase site.
Contains a API to return how many images are present of a particular subject and returns an image address corresponding to the images index, called by Image Viewer (below).
![]() Install ReCaptcha v3, JS fetch(), .NET Core, Website API's, JSON - Walkthrough (on arcaneww.com)
Install ReCaptcha v3, JS fetch(), .NET Core, Website API's, JSON - Walkthrough (on arcaneww.com)
 Woden Laundromat & Dry Cleaners: wodenldc.com.au
Woden Laundromat & Dry Cleaners: wodenldc.com.au
.Net Core 8
HTML, CSS, Media Queries, SEO
Woden Laundromat & Dry Cleaners Website.
Commercial site to display Opening Times and Details of a Laundromat in Woden (Phillip), Canberra, ACT.
Was originally wodenlaundromat.com which is now a 308 (Permanent Redirect) to wodenldc.com.au until renewal lapses.
 justinbentley.net: justinbentley.net
justinbentley.net: justinbentley.net
.Net Framework 4.8, Transact SQL (Stored Procedures), MVC, Razor
HTML, CSS, JavaScript, Bootstrap 3
Personal, First & Largest site.
 React: react.justinbentley.net
React: react.justinbentley.net
.Net Core 8, NPM, React
HTML, CSS, JSX, SPA (Single Page Application), <helmet>, emotion
Justinbentley.net Tours, Christmas in SVG & alternate page for ImageViewer.
No longer available due to comparatively high server costs, limited functionality and the deprication of the Create React App.
 Dennis Bentley Artworks: dennisbentley.net
Dennis Bentley Artworks: dennisbentley.net
.Net Framework 4.8, MVC, Razor
HTML, CSS, JavaScript, Bootstrap, React, JSX
Art Gallery.
Originally dennisbentley.net/gallery/sydney was written in clientside react and JSX though due to a unavoidable vulnerable package was rewritten in vanilla javascript.

 justinbentley.dev: justinbentley.dev
justinbentley.dev: justinbentley.dev
~ This Site ~
.Net Core 8
HTML, CSS, JavaScript, Media Queries, Intersection Observer API, Cookies
Light / Dark theme (using JavaScript) and Cookies to persist through sessions.
Intersection Observer API for <button> management.
Has a filter system that uses vanilla JavaScript and custom html 'keywords' attrib.
Filter accepts url params: justinbentley.dev?JS
* Favicon is dependant on light or dark theme.
 David Green Performances & Compositions: davidgreenmusician.com
David Green Performances & Compositions: davidgreenmusician.com
.Net Core 8
HTML, CSS, JavaScript
Davidgreenmusician.com is a site that hosts the musical compositions, performances and videos of David W. Green.
 Rendered Landscapes: renderedlandscapes.com
Rendered Landscapes: renderedlandscapes.com
.Net Core 8, MVC, Blender
HTML, CSS, JavaScript, WebGL (three.js), glTF (.glb)
Renderedlandscapes.com is a site that hosts and can optionally have created a real-time 3D render of an architectural structure (such as a pergola) which users can immerse themselves in and can walk around and view from all angles.
The CAD render files (or mesh's) can and have been created from Architectural diagrams, cardboard models or really ones imagination.
Server & Cybersecurity
AWS / EC2 Windows Server
AWS, EC2 (Lightsail), CloudFront CDN, Windows Server, IIS, MS SQL Server
Lightsail (EC2), Microsoft© Windows Server host.
IIS (Internet Information Services) for setting up https, hosting and binding sites,
SQL Server for hosting databases and most importantly executing the .Net Core runtime.
AWS Route 53 for (some) domain registrations, network records and nameserver setup.
CloudFront Distribution (AWS CDN) & AWS Certificate Manager (ACM) for very fast or high demand delivery of secure files.
![]() Setup automatic updates for .Net Core runtimes on Windows Server
Setup automatic updates for .Net Core runtimes on Windows Server
IIS Configuration
Windows Server, IIS, URL Rewrite, Failed Request Tracing
IIS (Internet Information Services) is the heart of Windows Web Publishing. Its the engine behind serving websites and content to the public on a Windows Server via the Web Server role and even underneath the surface in Azure.
There is an amount of configuration that needs to be done within IIS itself such as linking urls to hosts (Bindings), mapping directories within the server, configuring recycling/idle timers and amount of workers for each Application Pool process.
URL Rewrite is where all the URL magic happens. Here is where you can perform functions like redirection or denial on URL requests using absolute values or wildcards/regex.
Implements a vast array of black and white lists which has cut nefarious bots (such as looking for my .env files, not that they would be returned, if I even have them) by atleast 95%, this was eventually merged into GateKeeper (below).
Valid requests (such as .well-known/security.txt, a standardised link for security researchers) which I don't provide, a 404 is returned at the server level as opposed to having the Application try to process it, preventing a eventual 404 from waking the process.
Failed Request Tracing is where you can view failed URL requests (generally 404's, though sometimes 503 if you try and view a website in a state of publishing, oof). Using these traces and URL Rewrite (above) you can monitor what requests are not being fullfilled and redirect dead links, swat bots and gently guide the SEO crawlers to their proper target.
GateKeeper.dll,
GateKeeperAPI,
GateKeeperUpLink.exe
Web Application Firewall (WAF), Headless Class Library/.dll IIS Module, ASP.NET Core, .NET Framework, Windows Programming, C#, COM (Component Object Model), API, AbuseIPDB
After swatting bots in IIS UrlRewrite it became increasingly clear that I would need to write something dedicated to handle higher level request-filtering (in C#) and I also wanted to implement IP verification from the AbuseIPDB API.
GateKeeper.dll (Custom .NET IIS Module);
The purpose of the GateKeeper IIS Module is to intercept URL requests at a particular point in time within the IIS pipeline, after the main firewall, rate-limiter and URL Rewrite but before being served by the web server. Its a IIS module just like URL Rewrite and similarly it runs inline for each Application Pool (one instance per website).
At this point of interception it halts the request while it sends its details to GateKeeperAPI (below) which validates the IP using the AbuseIPDB records.
If the request makes it to this stage the GateKeeper Module will perform a variety of tests such a finetuned and maintained keyword blacklist (imported from URL ReWrite). If the request passes then it continues up the IIS Pipeline to the Web Server and if it fails the connection is dropped and the IP is reported, providing high quality reports (think zero-day IPs) to AbuseIPDB.
If the connection is dropped be it present in the Deny Table, filtered locally or dependant on AbuseIPDB records the GateKeeper Module will implement tarpitting (more below) but if the request is allowed the entire process takes easily less than 1/20th of a second especially if the IP is an allow entry in the GateKeeper module onboard cache.
GateKeeperAPI (ASP.NET Core API);
Orignally planned as a Windows Service using Named Pipes, for certain reasons (mainly named pipe permission escalation) it became a lightweight ASP.Net Core API site that listens only on localhost.
GateKeeperAPI's primary purpose is to store and maintain Black and Whitelisted IP Tables.
As the GateKeeper modules recycle and are inherantly short-lived they lack the ability to maintain IP Tables and as they are run parallel in isolated Application Pools an IP that requests multiple sites would have to be reverified for each.
GateKeeperAPI solves this by maintaining a cache of IP's stored in memory and being always-on can store them for an arbitrary length of time.
It populates these tables from the AbuseIPDB databases via an API (thankfully situated 1ms away at the same AWS datacenter as the server) and also reports IPs to AbuseIPDB if requested from the GateKeeper Modules. If a report occurs the IP entry is overriden to a Deny and will be locked out for a period of time.
GateKeeperUpLink.exe (.NET Console);
Thanks to pure serendipity, having the IP Tables present in GateKeeperAPI made making a real time monitor of server activity an elementary task.
GateKeeperUpLink communicates with GateKeeperAPI on a localhost port to retrieve the current IP Table information. It then queries AbuseIPDB for each entry which provides details such as what is making the request (Proxy, Search Engine Crawler), who and (potentially) where. This provides valuable information about who is accesing the server in realtime which for the most part ensures the blacklists are working properly but can also tell me if the server is being bombarded (which is not uncommon for any website/server).
On a base Windows Web server
Outcome;
The main purpose of all this (which started ages ago with URL Rewrite) is to disincentivize Vulnerability Scanners, in other words counter automated scanners that over-time try to break into systems by finding critical files (a surprisingly common and persistant practice on the internet).
The effects of this generally pointless (and oft-times amusing) endeavor is to divert computer and network resources from valid duties and in some instances (such as pay-as-you-go) lead to real costs involved to entertain these activities.
There are also hard cyber measures that this system performs that are effective against both vulnerability scanners and actual threats;
As the local keyword blacklists were offloaded from Url Rewrite into GateKeeper any programmatic function can be performed utilizing them including a technique known as Random-Time Tarpitting (waiting a random amount of time before severing the connection) which eliminates time-based attacks, ceases differentiation between a Keyword and AbuseIPDB Abort and locks-up the scanners resources in return.
Also, in contrast to URL Rewrite (which would abort on a per request basis) if an IP trips the local blacklists it's added as a deny entry to the IP Tables (and sent to AbuseIPDB), blocking the IP at the proverbial front door for next time and preventing repeat filtering of a abusive IP. In addition to this and also in contrast to URL Rewrite an Abort can create a log, either custom or in Failed Request Tracing, of which I've set up custom HTTP codes to interpret the reasons why it was blocked.
Lastly, the most significant feature of AbuseIPDB is its ability to identify compromised or malicious IP's before the requests arrive (a function I cant perform locally) and this provides a effective counter to scripts that roll a new IP for every request.
AbuseIPDB Profile, all requests reported by GateKeeper, since August 2024.



Schematics, Integration into a IIS Web Server (left to right):
GateKeeper V1 Original Self Contained Standalone version,
GateKeeper V2R1 (currently implementated) using instanciated IIS Modules, a ASP.Net Core API and Utility programs,
Diagram of interaction between GateKeeperAPI, GateKeeper IIS Module/s and AbuseIPDB.








GateKeeper components in action (left to right):
GateKeeperAPI being accessed by curl (with IISOnline and AbuseAPI, the prototype AbuseIPDB query engine used by GateKeeperUpLink and GateKeeperAPI),
GateKeeperUplink (x2),
Manually blacklisting myself via a curl command to GateKeeperAPI,
Under Attack during a Brute Force Vulnerability Scan combined with a semi-DDOS (x2),
Server shutdown during a GateKeeperAPI upgrade,
Custom Headers introduced by the GateKeeper module.
File Server (.Net Core): fs.jbn.ai
.Net Core 8, API, AWS CloudFront, CDN
.Net Core file server completely coupled to the AWS CloudFront Content Delivery Network.
Always on file server acting to serve files used by multiple sites (ie ImageViewer, cookies.js, below) and/or serve files quickly or at a very high bandwidth.
Also, being always on serves intermediatary functions such as resolving urls like fs.jbn.ai/rd/youtube-channel and a image server for ultra high quality images on sites like linkedin (superceeding jbn.ai, which superceeded justinbentley.net).
In addition to GateKeeper it also implements its own suite of security measures such as discriminate file Rate Limiting and selective CORS.
Server Tools


 IISOnline
IISOnline
C#, .Net Core, Windows Server, IIS
When monitoring the Server its challenging to know which loaded IIS Workers belong to what website, so I made a program to do that.
IISOnline queries IIS for Application Pools and stores their names and status. Then queries the command lines of running IIS Workers for a hostname match and if found displays their PID/s (Process Identifier).
Its finetuned to use as little RAM as needed, hence the "any key to rescan" option and specific command to refresh IIS Pools. Though if resources are not at a premium it also has an auto-scan mode.
github.com/jubentley/iisonline
![]() IISOnline (IIS Web Workers, Windows Server Processes, C#)
IISOnline (IIS Web Workers, Windows Server Processes, C#)





 FRTLibrarian
FRTLibrarian
C#, .Net Core, Windows Server, IIS
FRTLibrarian accesses Failed Request Tracing logs from within the Windows Server filesystem. It analyses the logs one by one, extracts specific data and tabulates entries in a chronilogical order.
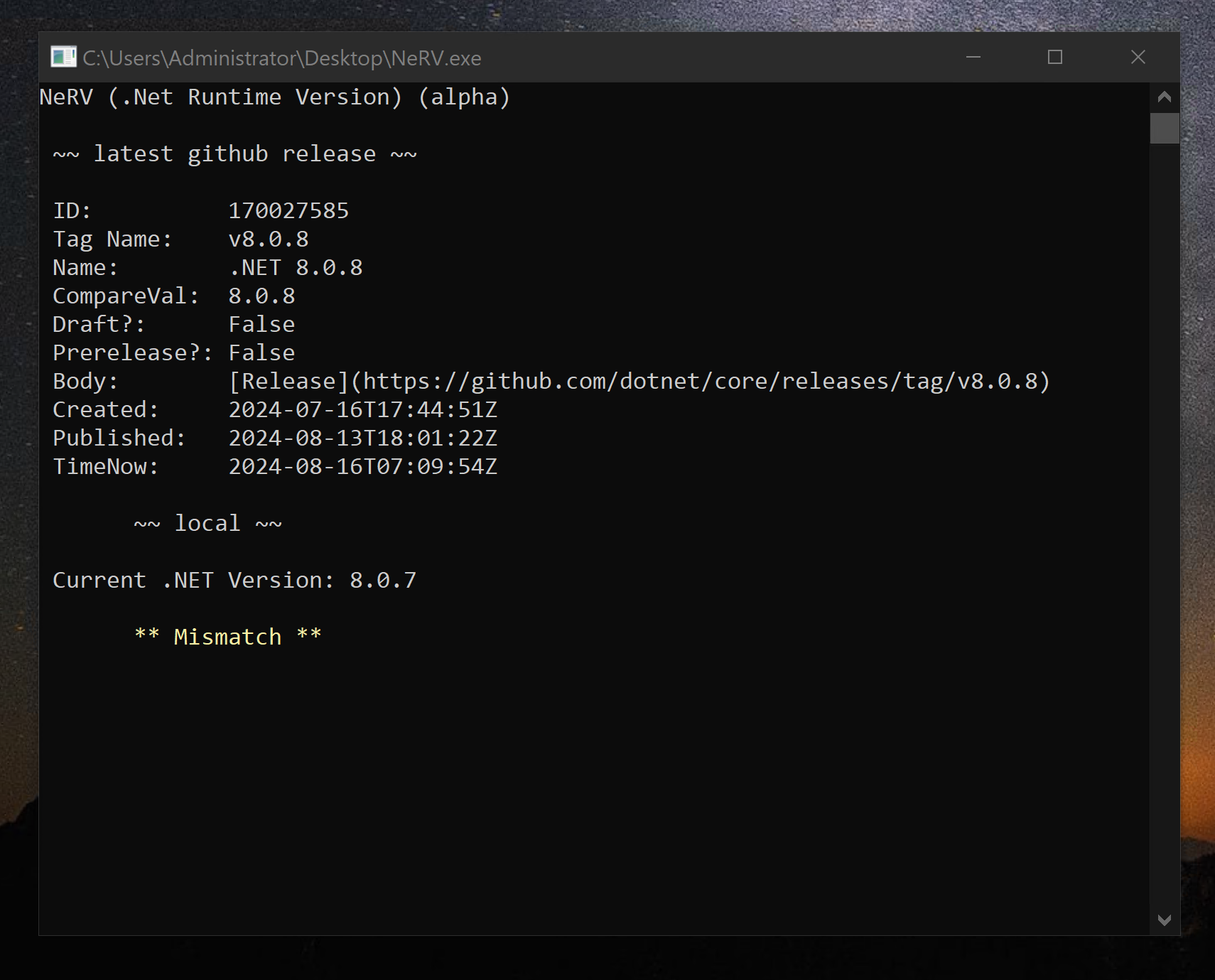
 NeRV (.Net Runtime Versions)
NeRV (.Net Runtime Versions)
C#, .Net Core, Windows Server
Queries the Github API for the latest .Net runtime version and queries the local system for the current version.
If the versions do not match (ie there is a later version available) NeRV can display this to the user if run in real-time or if run by the Windows task scheduler can send an email to an admin or autonomously install the update.
Subsequently the .Net Core runtimes have been registered into Microsoft Update and this program has become mostly redundant though its still used for update verification.

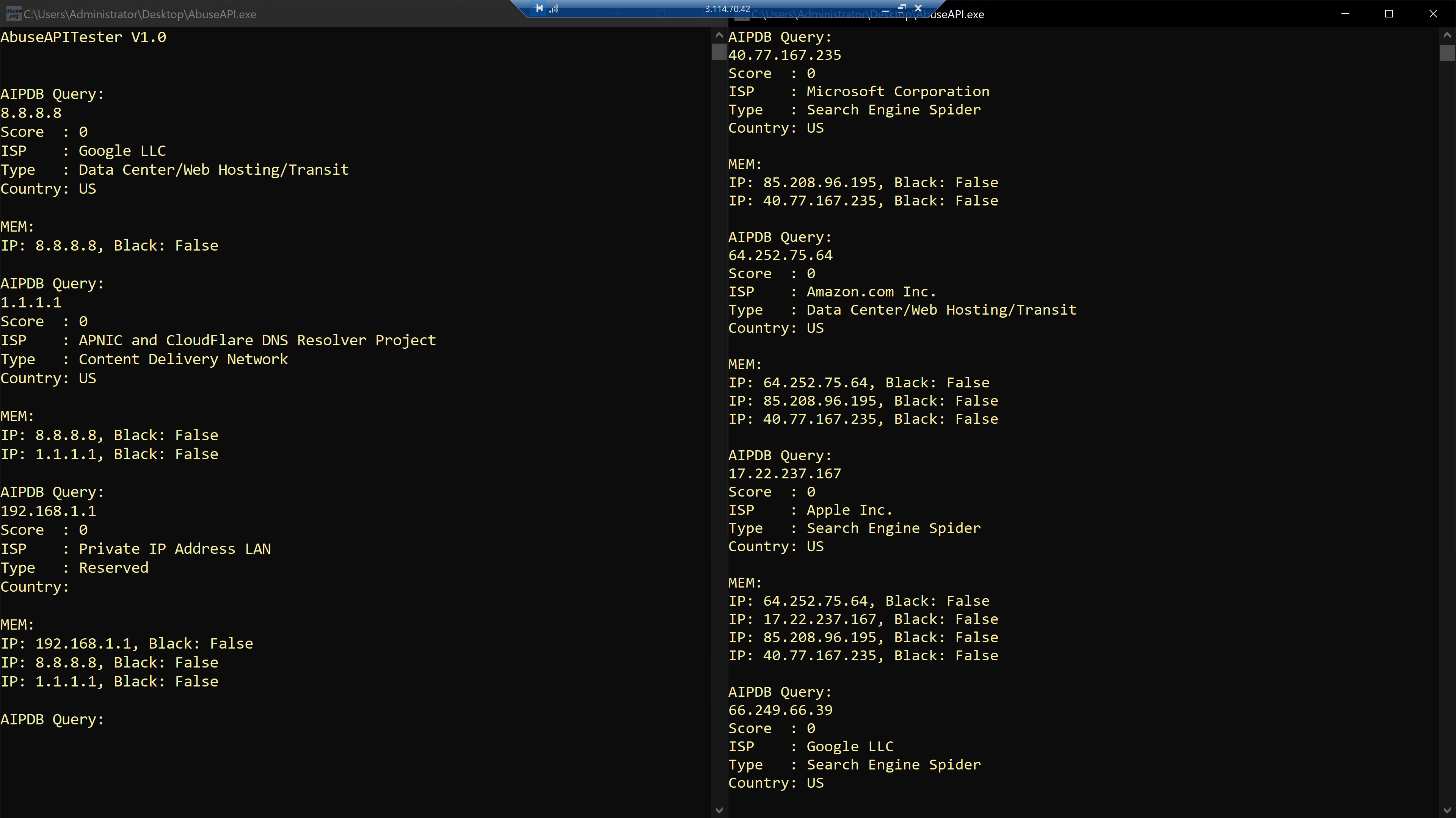
 AbuseIPDB API (Tester) / AbuseIPDBQuery
AbuseIPDB API (Tester) / AbuseIPDBQuery
C#, .Net Core, WebAPI, AbuseAPI
One thing that was absolutely clear was that the GateKeeper IIS Module was a serious pain to create. Being a resource limited server meant no local programming despite requiring some server applications, being a .dll meant no debugging and manual entry into the GAC and a ton of not particularly simple settings, and being ran in a secure virtualized environment (App Pool, IIS Pipeline) meant no logging (without localhost HTTP), no access to the file system, no access to named pipes and no API.
Therefore what was of prime importance was to firstly have functioning and verfified blocks of code to perform the tasks required before, the brute-force implementation.
I ended up using AbuseIPDB API (AIPDBQuery) to create the AbuseIPDB API Caller and Memory Caching strategy which became a part of the GateKeeper IIS module and was later ported to the GateKeeperAPI ASP.Net Core localhost site.
github.com/jubentley/AIPDBQuery
JS Utility Scripts
ImageViewer.js
JavaScript, API
Standalone Full-Screen Image Viewing Script featuring a variety of features and zoom limited only by the resolution of the Image.
Currently its over 1000 lines of JavaScript and 300 of CSS.
ImageViewer (IV) has three modes of operation:
- Start IV with a single Image.
- Start IV with API support, firstly IV requests a number from an API representing how many images available for target item, then IV requests a src using the item number and item index, then IV starts using the src and displays left and right buttons to cycle through the items repeating the latter API call.
- Start IV with simple Array support, functionally the same as API support though an array of src's and a index can be referenced instead.
Certain settings can be set before IV is started such as show demo buttons (unsplash and image galleries), demo LR buttons (unsplash, a third party random image API), LR button title text, the Start IV with API support API base addesses and Invert Zoom.
Lastly, uses a complicated mathematical algorithm that I designed to keep the image anchored in the middle of the screen while zooming in or out, otherwise the image will zoom but the top and left point will remain anchored in position.
Used for arcaneww.com (which was the host of the script before the dedicated file server(above)), react.justinbentley.net, dennisbentley.net, justinbentley.net and justinbentley.dev (click on an image on this site to use).
ImageViewer can be found running here: justinbentley.net/image
Or by clicking any image within arcaneww.com, dennisbentley.net, justinbentley.net or this site.
glparticlegen.js
JavaScript, WebGL (three.js), GLSL (C),
Created my own particle system to work in tandem with 3D (WebGL) scenes. It contains a JavaScript polymorphic super class with two child classes to operate different types of particle shaders and my own GLSL (C like GPU code) Shader code to bring it all together on the GPU.
Currently used for jbn.ai and jbn.ai/webgl though has future plans.
The source code can be found here: jbn.ai/js/glparticlegen.js
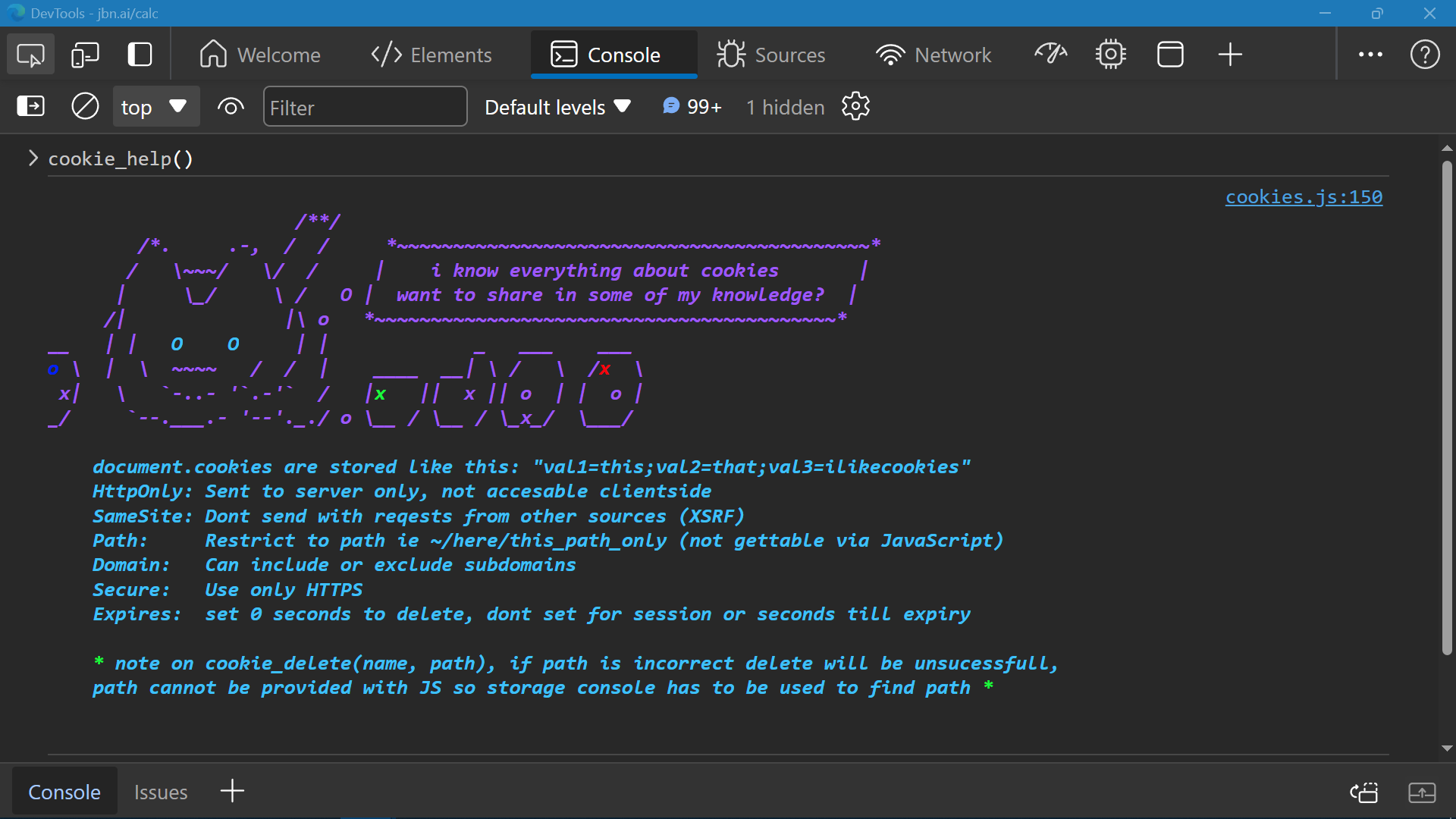
cookies.js
JavaScript, Cookies
Standalone script to handle Cookie operations.
Used for many of my sites and centrally located on the file server.
This site uses this script to store data to persist the light/dark mode preference between reloads and revisits.
fs.js
JavaScript
Standalone script to handle Fullscreen operations.
Used for many of my sites and centrally located on the file server.
Database
SQL / T-SQL / MSSQL Database
SQL Server, SQL Table Setup, SQL Monitoring, SQL Stored Procedures
Secure and highly streamlined SQL Database that runs my own relational tables and stored procedures.
* SQL, SQL Server, T-SQL & MSSQL is the same thing.
Database Security, justinbentley.net/pentest
SQL Stored Procedures (vs) Pentesting Tools
After creating the Database I decided to run it through a Pentest and verify it's Security.
3D Application Graphics Programming
VR Tai Chi
C++, OpenGL 4.4, GLSL 4.4 (modified C), x64, Steam Corp OpenVR <openvr.h>, Autodesk Maya, GLFW, GLEW, GLM (Math / Quaternion Library)
Scratch made OpenGL Modern Renderer, Game, Tai Chi Simulator in VR with Autodesk Maya constructs.
Game Engine, Game, Models (mesh), Mesh Importer (.obj), Digital Elevation Model (DEM) / Heightfield Importer, Shaders, Keyboard & VR Device Control.
![]() University ICTP Project - VR Tai Chi (C++, Modern OpenGL, SteamVR)
University ICTP Project - VR Tai Chi (C++, Modern OpenGL, SteamVR)
Microsoft© Bubbles Screensaver Clone
C++, OpenGL 3.3, GLSL 3.3, x64
Clone of Microsoft's most popular screensaver ever!
Created to learn 'modern' OpenGL and was a milestone in VR Tai Chi (above).
VIC Final Assignment
C++, OpenGL 1.2, GLUT (GL Utility Toolkit), Autodesk Maya
Scratch made Legacy (90's) OpenGL Renderer, Game World Logic and Programatically made assets.
Game Engine, Game, Digital Elevation Model (DEM) / Heightfield Importer / Renderer (whitespace seperated .txt), Mesh Importer, Keyboard / Mouse Control.
University of Canberra Unit, final grade High Distinction @ 92/100.
.obj Wavefront Mesh Importer
C++, OpenGL 1.2, GLUT (GL Utility Toolkit), .obj Mesh File
Importer to turn a 'mesh' created in a CAD type program into triangles to be displayed in my own real-time Renderer.
Legacy (v1.2) OpenGL Guide
C++, OpenGL 1.2, GLUT (GL Utility Toolkit)
1.5 hour tour of OpenGL 1.2, one of my most popular Youtube Videos.
Training Room (Autodesk Maya)
3D Mesh, Autodesk Maya.
3D Assets for VR Tai Chi.
![]() Autodesk Maya - Make a Simple 180 Degree Skybox/Skydome + UV Editing
Autodesk Maya - Make a Simple 180 Degree Skybox/Skydome + UV Editing
2D Programming
USS-199
C#, XNA / Monogame
Game Engine, Game, Keyboard / Mouse Control, Scoring, etc.
All game assets made in Paint.net!
Save the Trees
C#, XNA / Monogame
Game Engine, Game, Keyboard / Mouse Control, Scoring, etc.
First Game Ever!
May not be the most complex, but was made in the University of Canberra library late into the night and weekend after the very first tutorial!
File System Programming
CodeLiner
C++, Win32API <windows.h>
Extract lines of code / operations from .cpp, .c & .h file found in a specified windows directory.
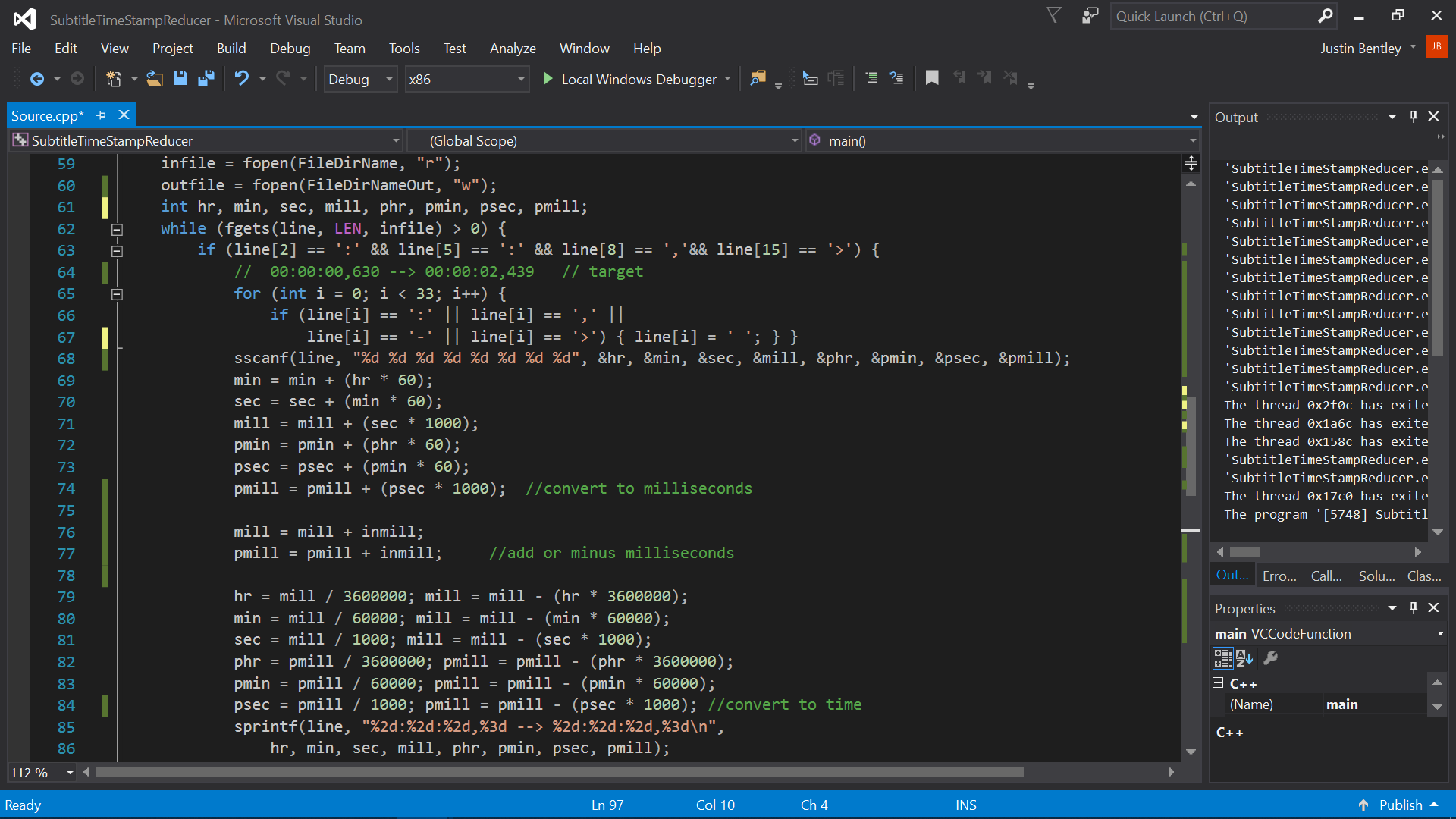
Includes a complicated algorithm (second pic) to test for multiple operations per line and ommit comments.
Uses <windows.h> to query a directory (third pic) for .cpp, .c & .h files.
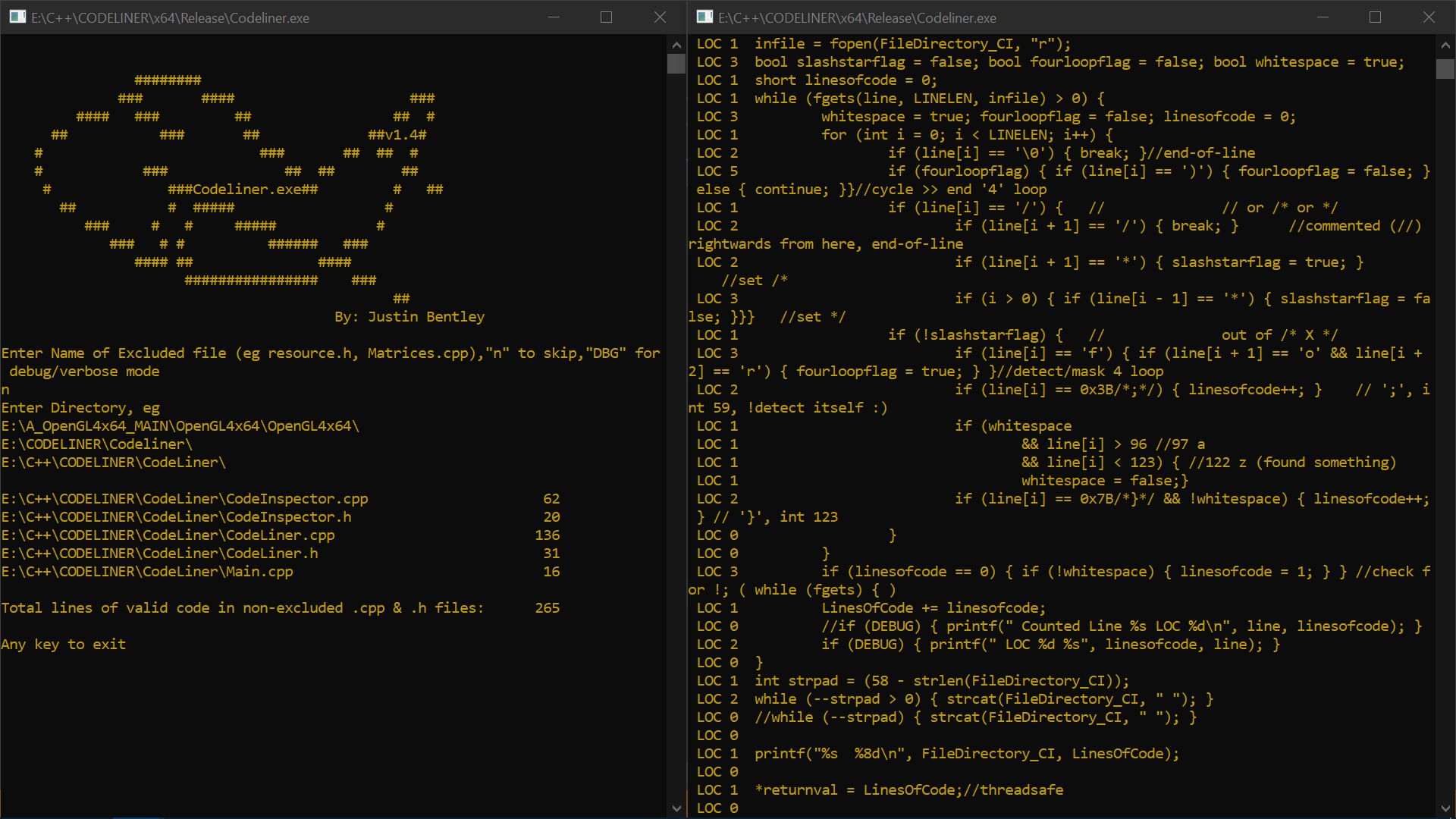
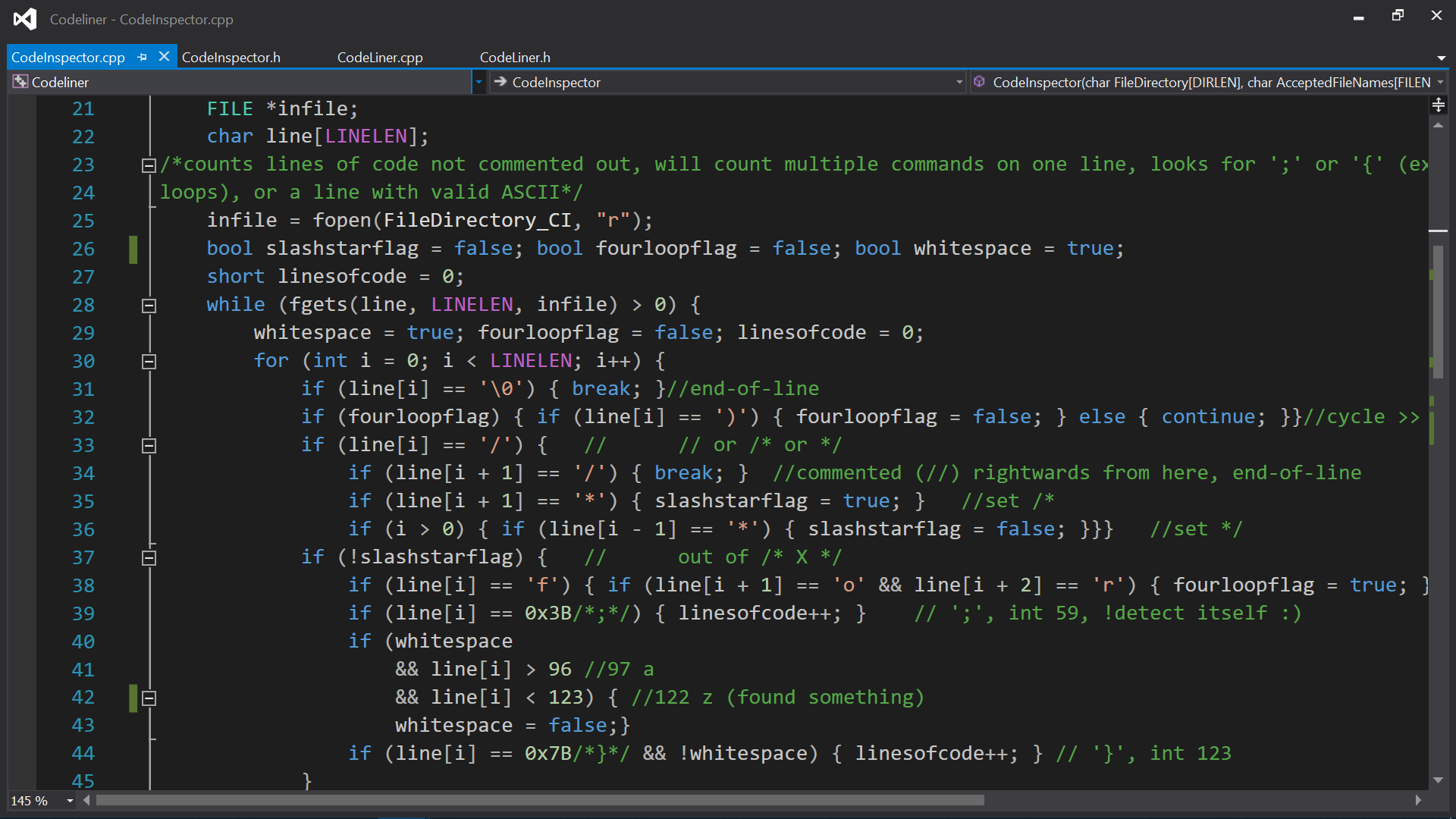
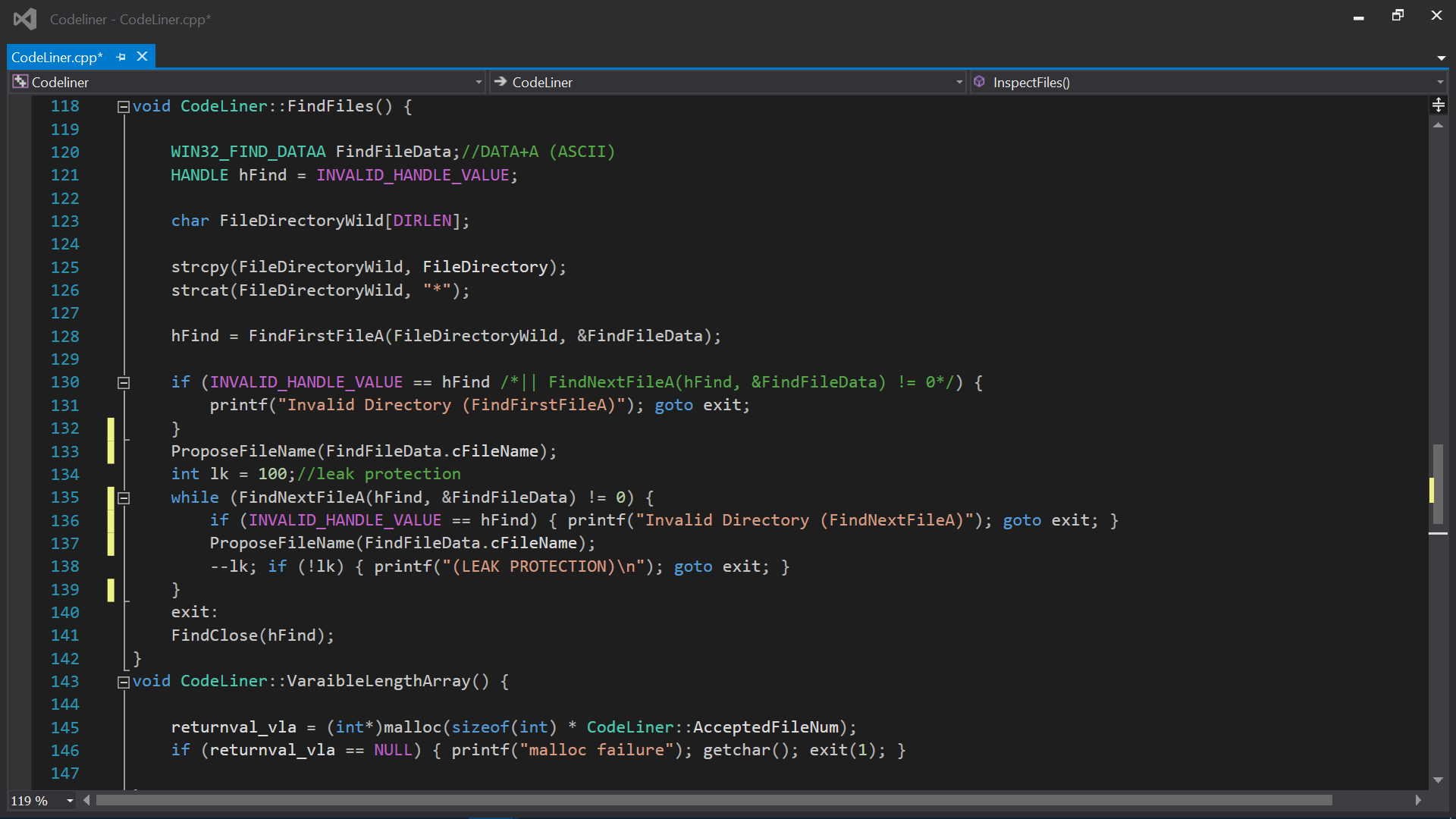
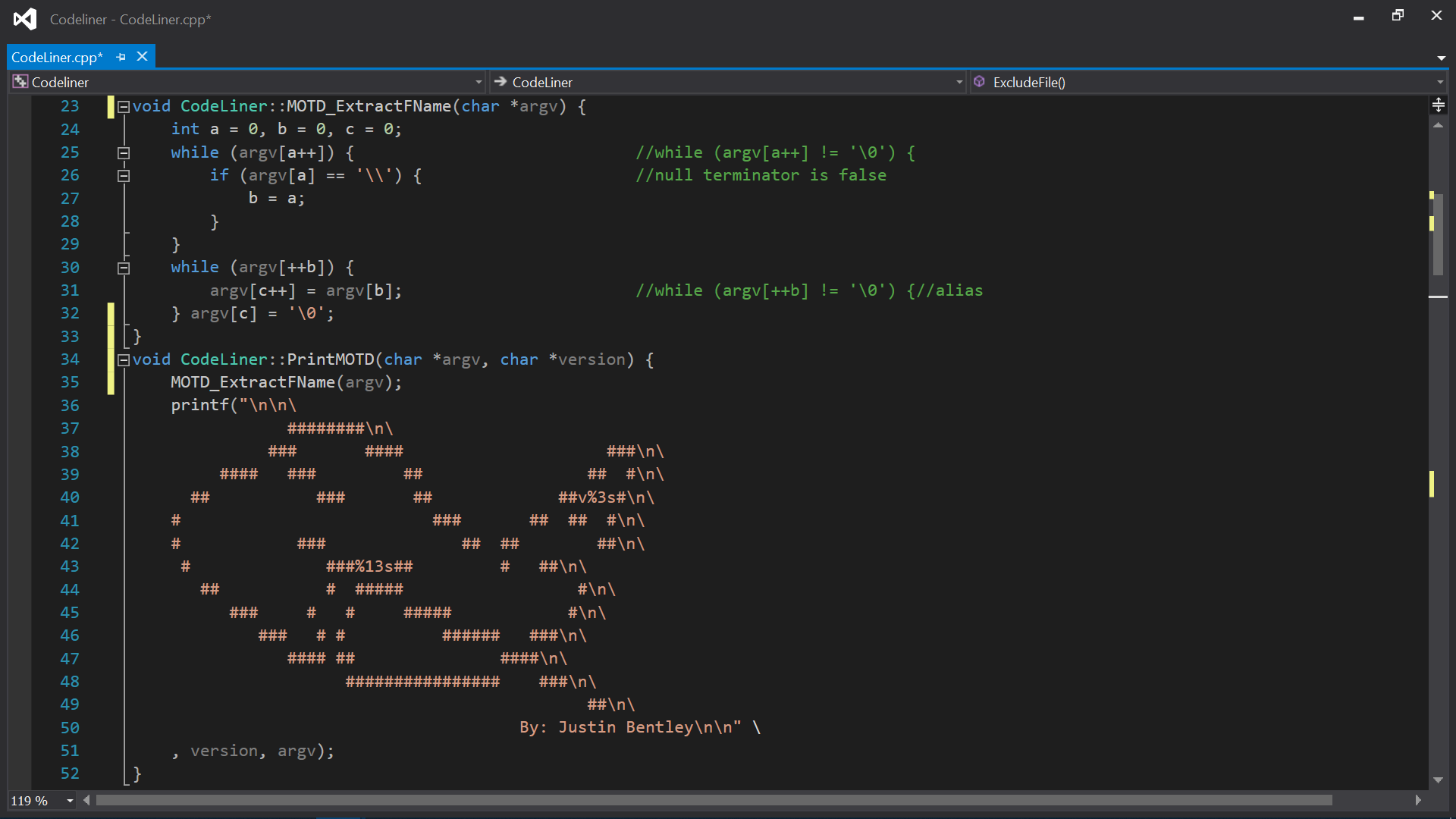
CodeLiner Report on itself in DBG mode and some snippets of the code.
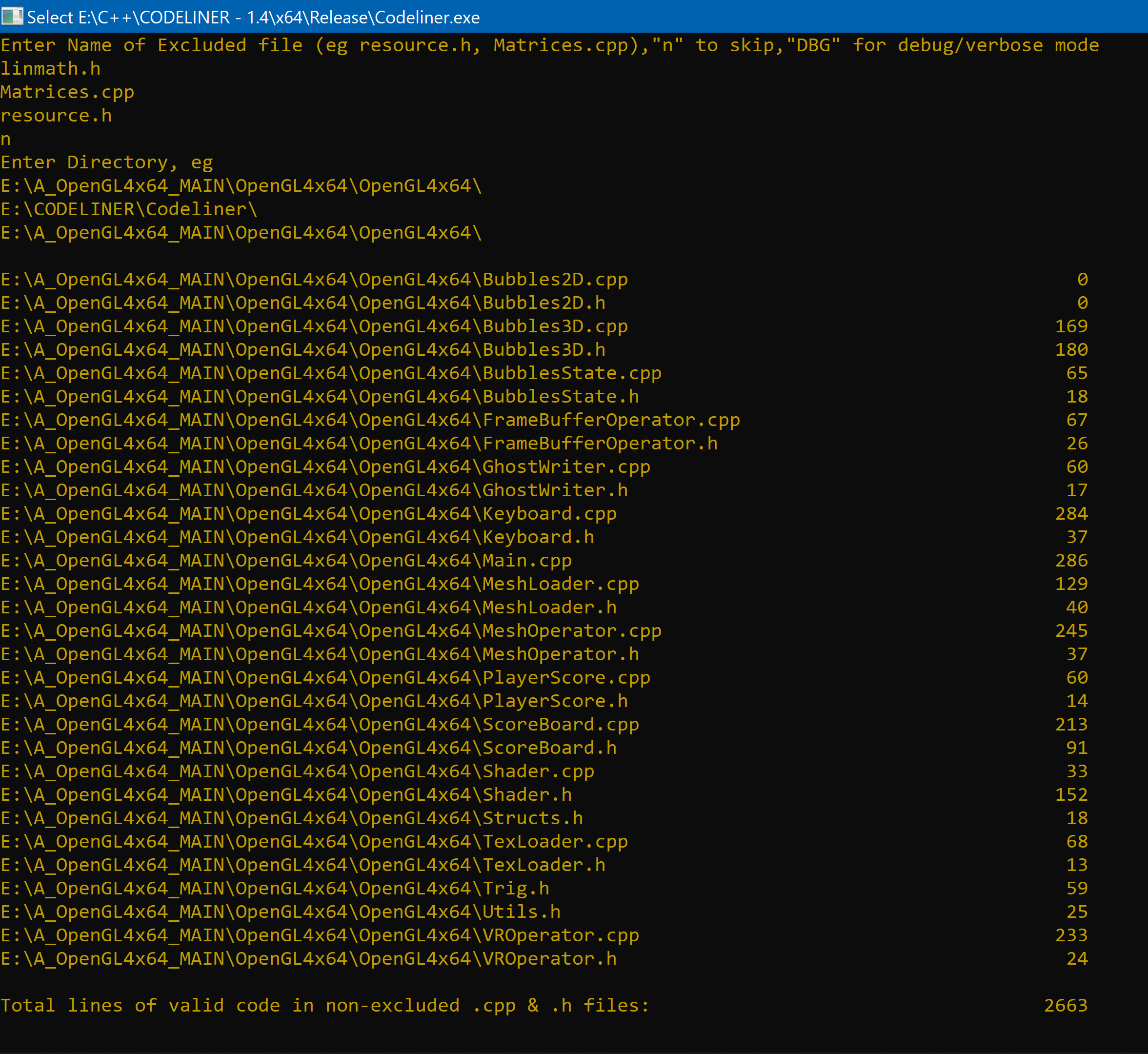
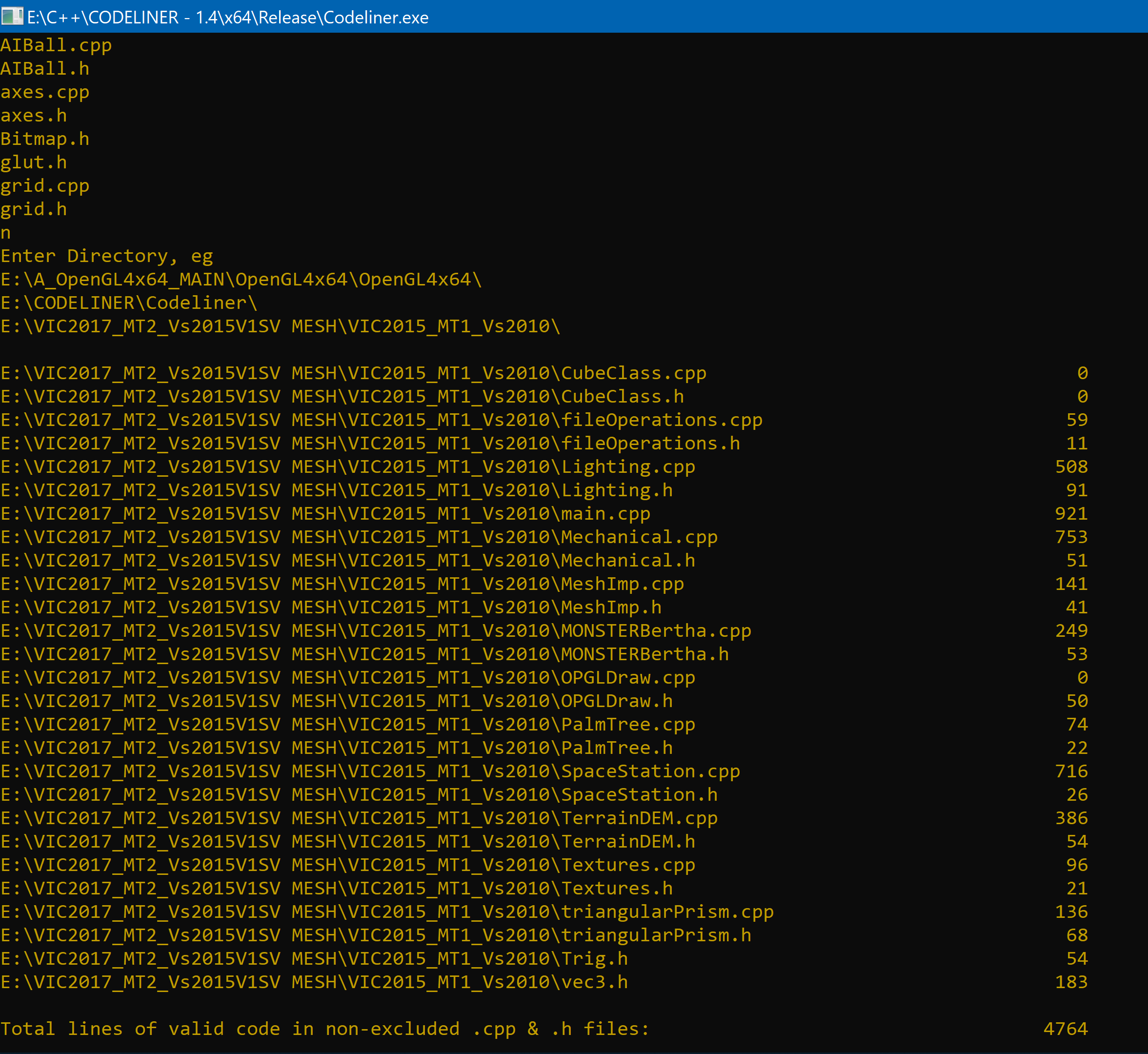
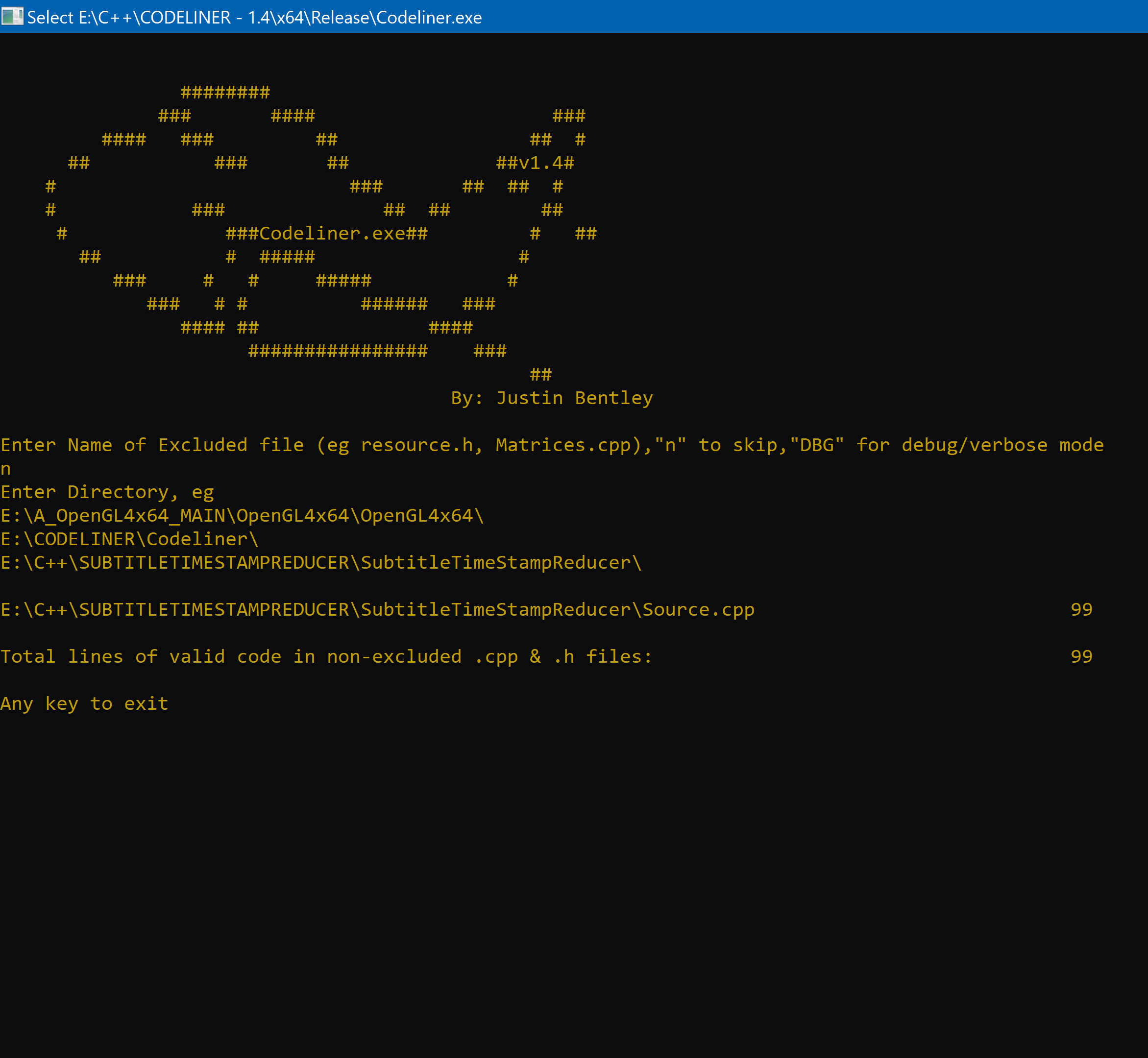
CodeLiner Reports on some of my C++ Programs (left to right):
VR Tai Chi
VIC Final Assignment (Legacy (v1.2) OpenGL Guide)
Subtitle (.srt) Time Stamp Reducer
* If your wondering why is VIC Final Assignment (a relatively simple legacy OpenGL game) much bigger than VR Tai Chi (A entire Modern OpenGL Simulator with VR) its because VIC uses glPush, glTranslate, glDrawCylinder to draw everything (and it even holds angle variables/joints in the right place), until the .obj mesh importer came out to bring assets in from Autodesk Maya.
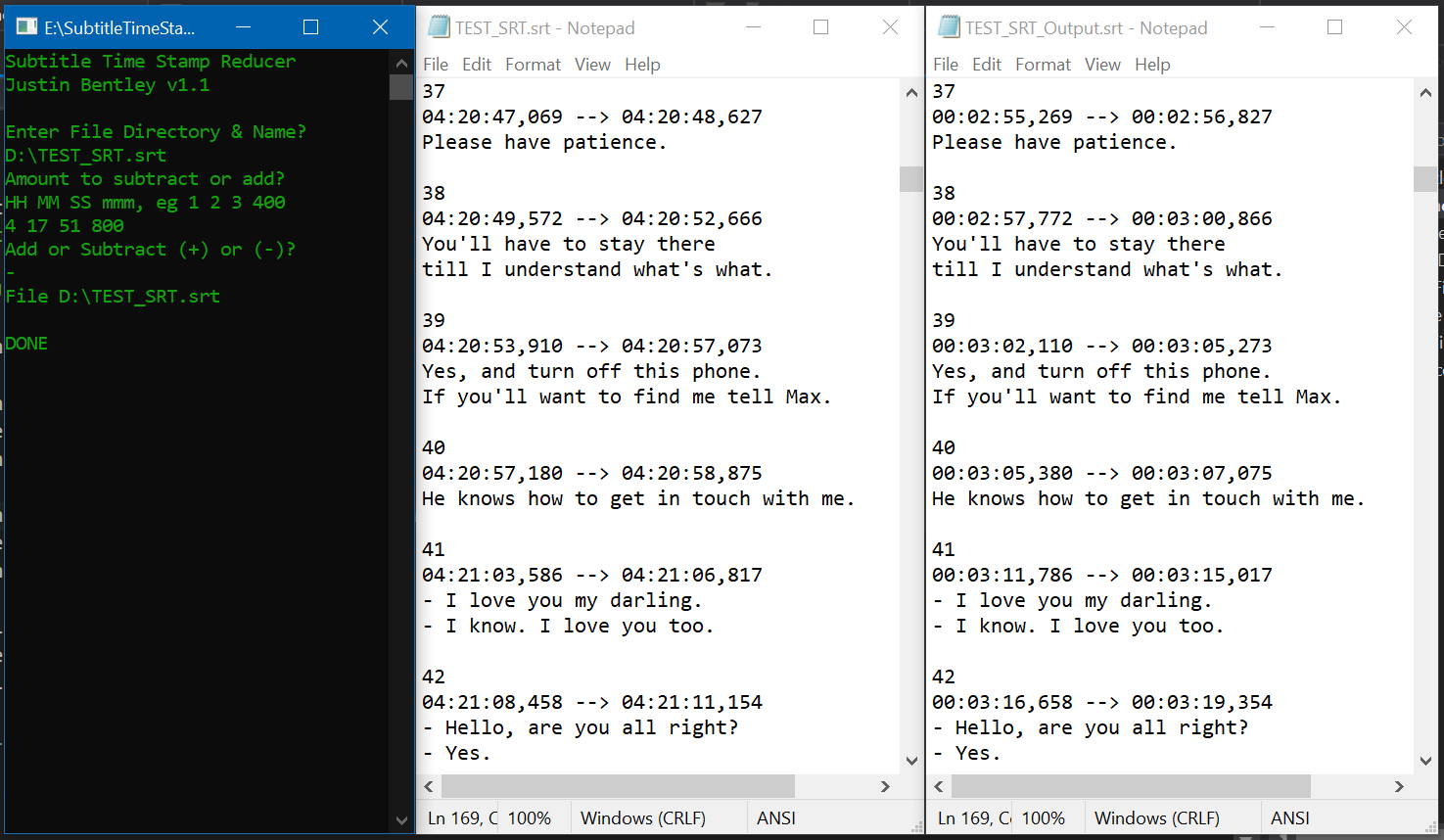
Subtitle (.srt) Time Stamp Reducer
C, POSIX
Globally reduces or adds to timestamps of a .srt (Video Subtitle) file.
github.com/jubentley/SubtitleTimeStampReducer
Payroll System
C, POSIX
Program to organize the payroll operations of a business and 'printf' payslips.
Application Programming

 Sleep
Sleep
C or C# Application
Trigger a monitor power down state on command.
Your watching television while using your Laptop or PC, something good comes on, you can use this application to temporarily turn the montor/s off.
This application does not put the system to sleep, it only triggers the monitor power down event and moving or clicking the mouse will wake them back up.
Sleep comes in two varieties (and two different icons), written in Native (C) or Managed (C#) code, the executables can be found in the repositories below:
Gross Calculator
C# Form
Salary, Taxation, Super Calculator.
Predecessor & engine of: justinbentley.net/salcalc
ANN (AI) 1
C# Form
Front-End for a C++ AI (Artificial Neural Network) Back-End Engine to input training data and values.
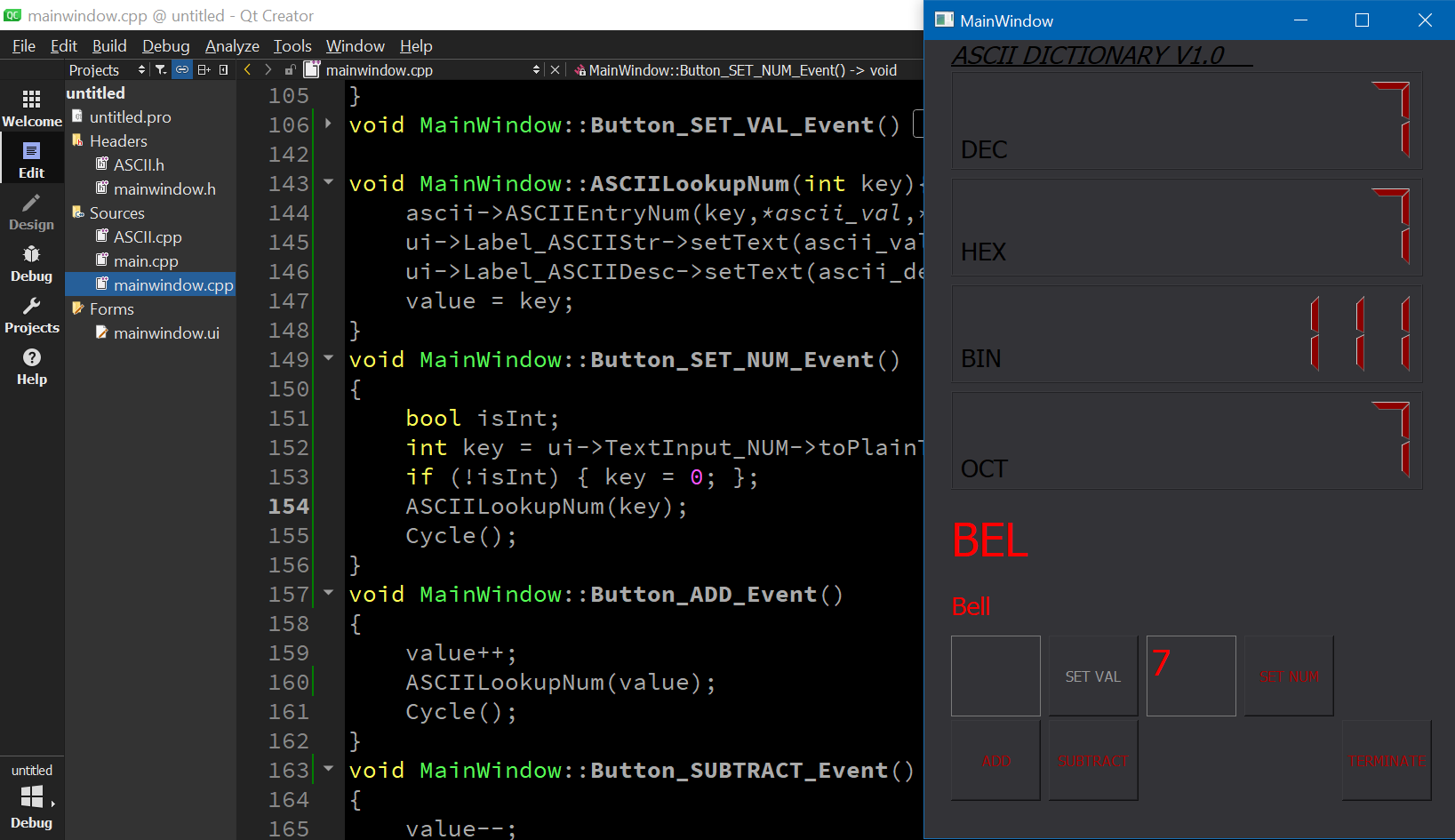
ASCII Dictionary
C++, Qt Creator
Provides decimal, hexadeciaml, binary & octal values for a entered decimal or character ASCII (utf-8) value.
Very similar to Android Studio.
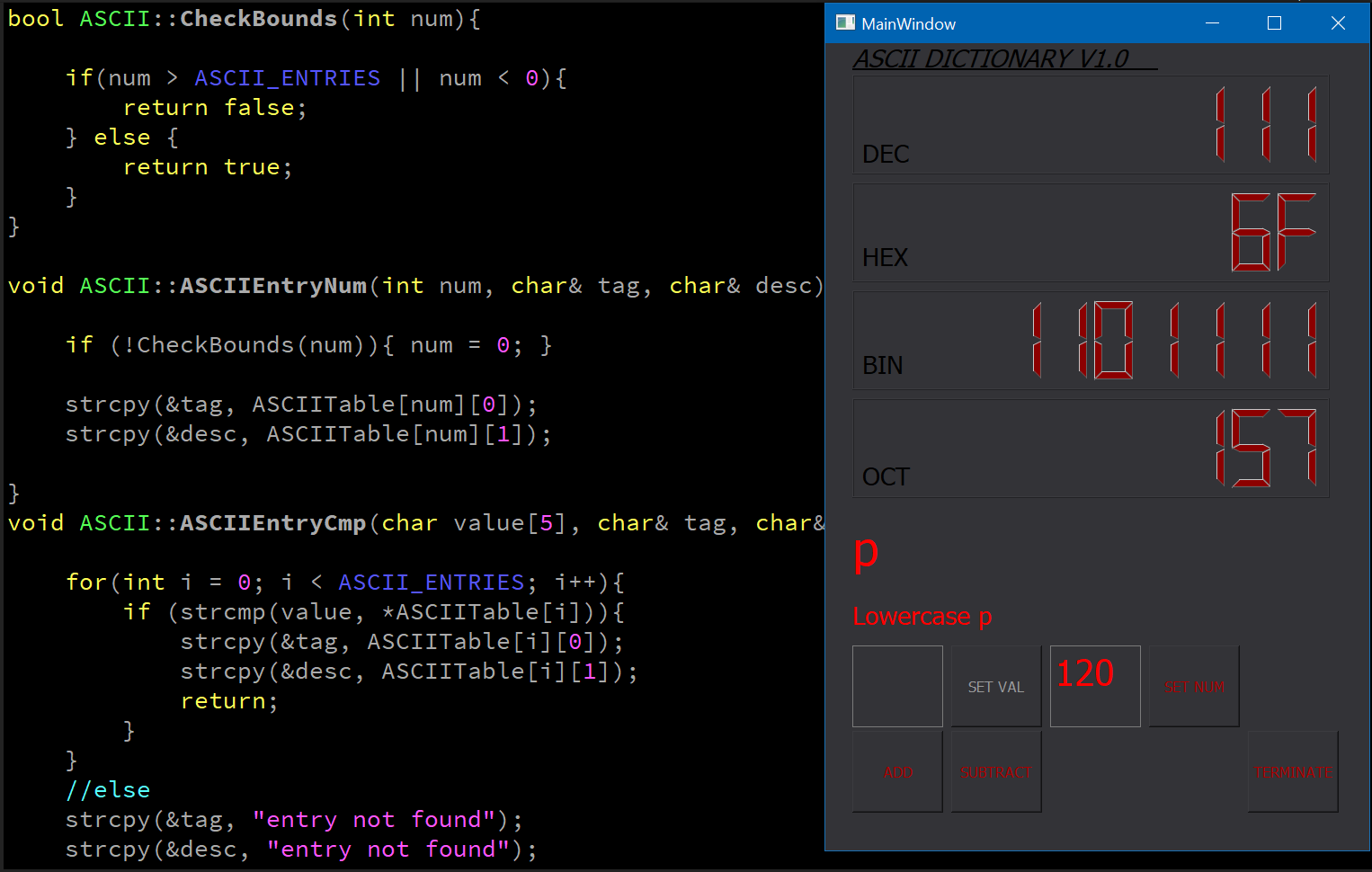
Timer
C++, threading
Queue's alarms within Windows for entered times.
Testing
xUnit
xUnit, C#, WebAPI, .Net Core
I thought I might as well try out some Testing Frameworks, decided on xUnit.
github.com/jubentley/NeRV (Includes xUnit Tests)
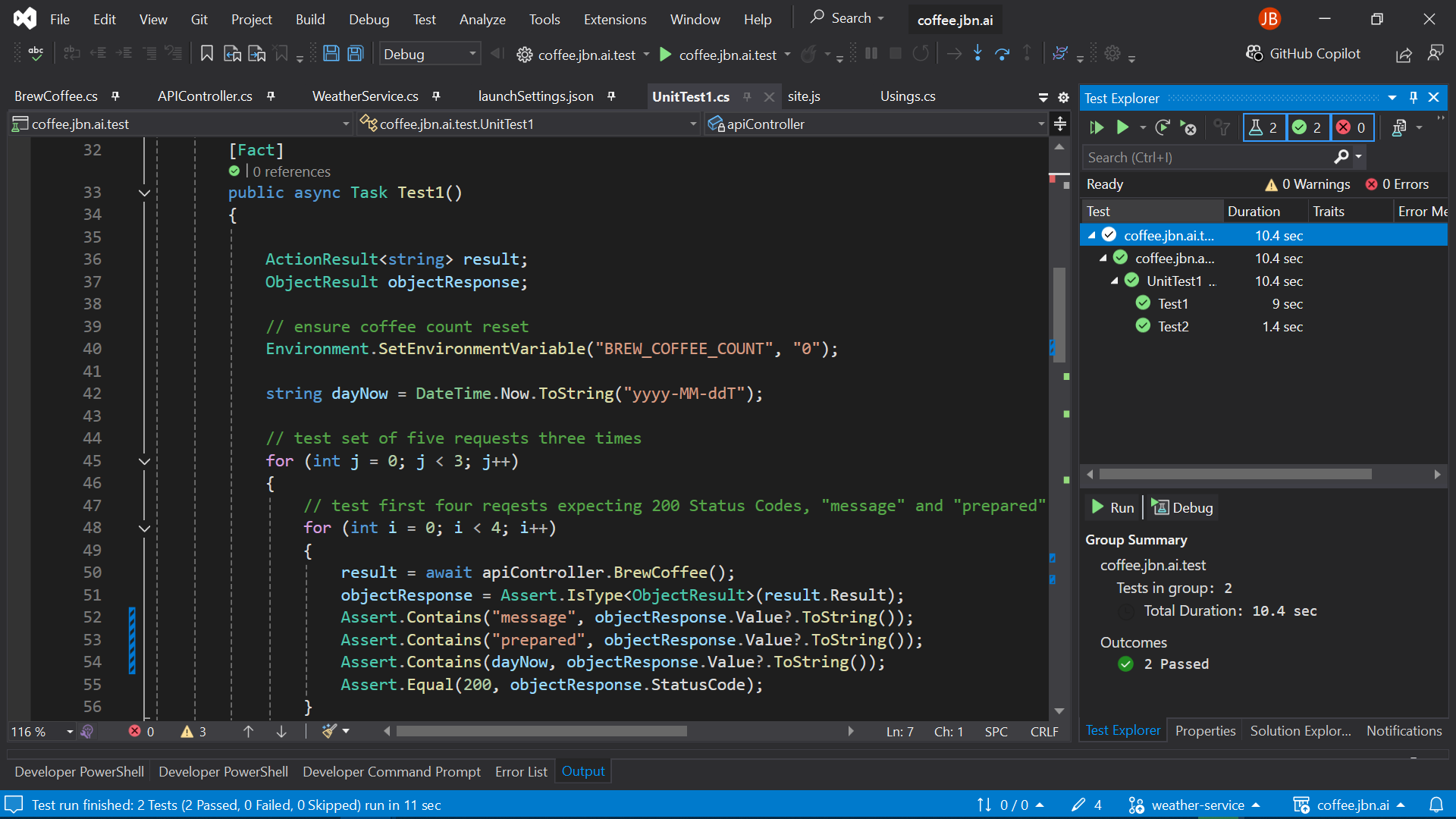
Other
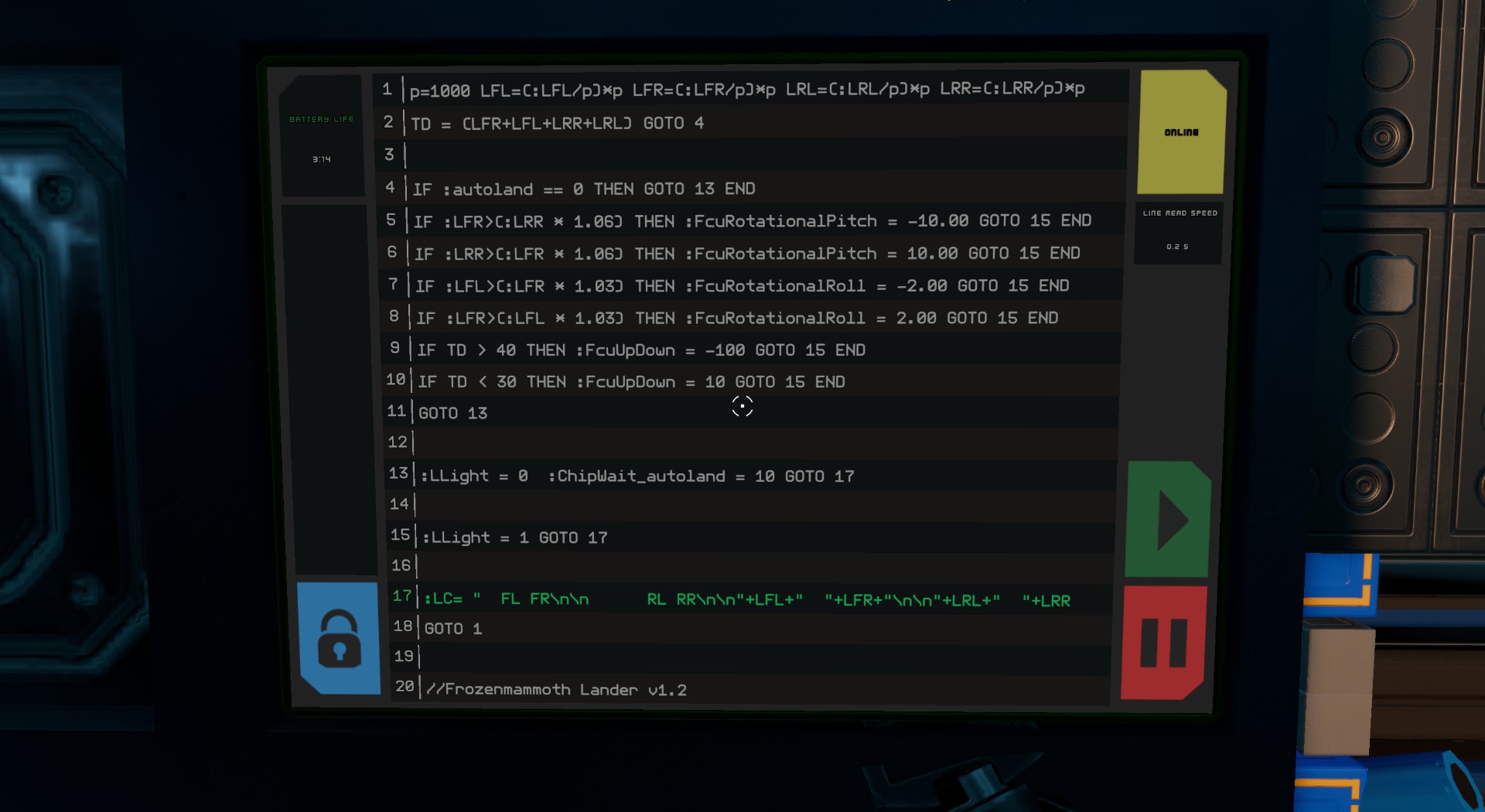
StarBase BASIC
BASIC
Not quite your traditional BASIC programming but anyway, theres a MMO Video Game called Starbase where you build a Space Ship and use the Programming Language BASIC to enhance its systems.
Autogen would run the Power Generator to feed the Battery, although it was a bit more complex, it would add load to the Generator if the Battery was less than its last cycle reading and vice versa. Also, add or remove load if the Battery was below or above particular limits, forming a sort of heuristic with weights.
AutoLander would adjust the Pitch & Roll of the vehicle until Rangefinders at each corner of the undercarriage were showing similar distances, indicating the ship is level. Then it would adjust altitude until a particlular range was reached, all while activating the Landing Lights.
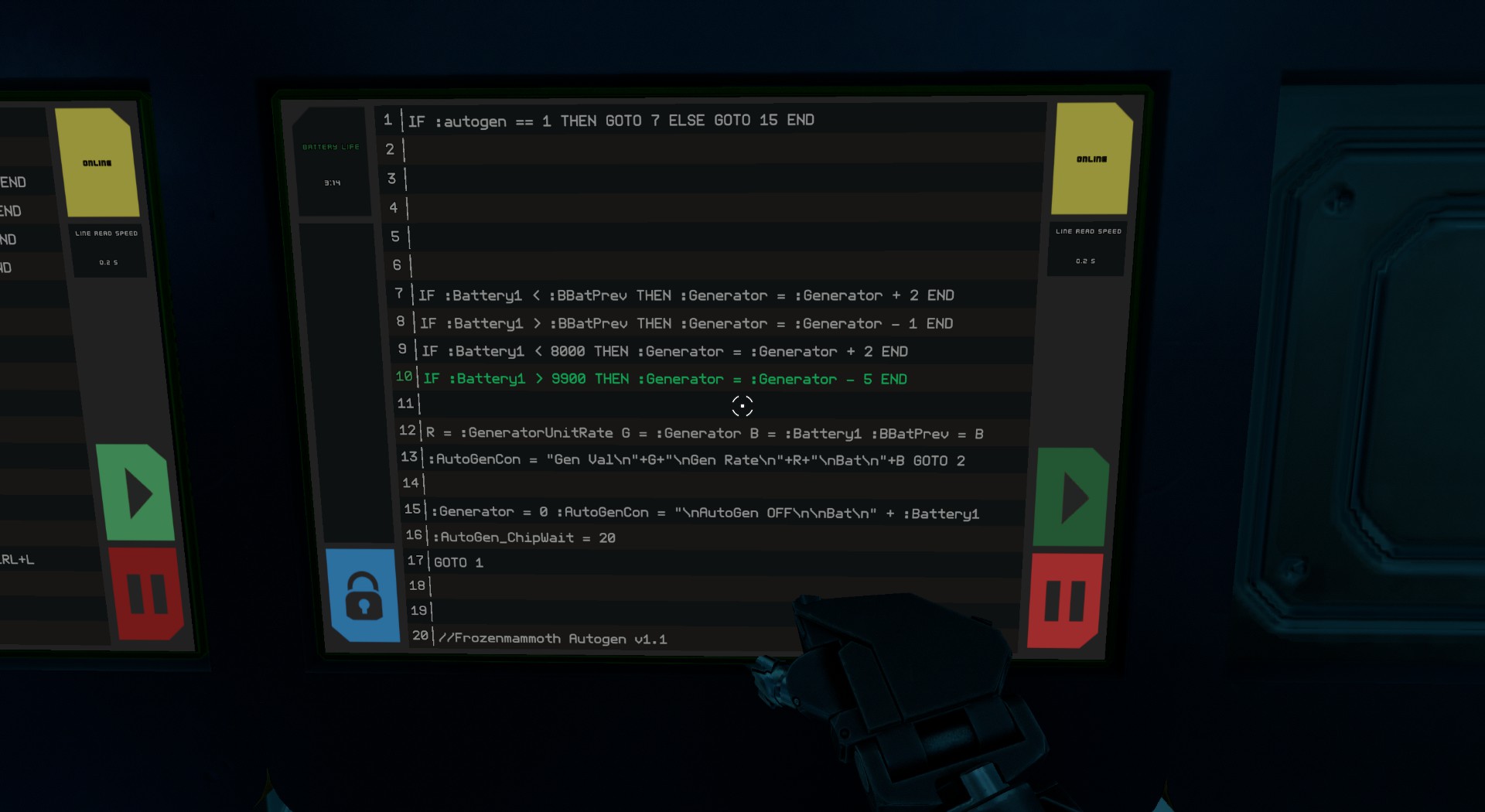


Very Long URL Expertise: justinbentley.net/veryveryveryveryveryveryveryverylongurlexpertise
Were you expecting the url to overflow the right margin?
Important component of a youtube video I made addressing a common Web Development topic, ever seen a website that scrolls left to right and wondered why?
The link above is clickable, or alternatively;
![]() CSS - Overflow Right Margin - Horizontal Scroll Bar appearing
CSS - Overflow Right Margin - Horizontal Scroll Bar appearing